Some Internet specialist organizations and corporate organizations may have blocked the greater part of the ports, and permitted just a couple of particular ports, for example, port 80 and 443 to fix their security. In such cases, we must choose between limited options, yet utilize the same port for different projects, say the HTTPS Port 443, which is once in a while blocked. Here is the place SSLH, an SSL/SSH multiplexer, comes in offer assistance. It will tune in for approaching associations on a port 443. To put this all the more just, SSLH enables us to run a few projects/benefits on port 443 on a Linux framework. In this way, you can utilize both SSL and SSH utilizing a same port in the meantime. On the off chance that you at any point been in a circumstance where most ports are obstructed by the firewalls, you can utilize SSLH to get to your remote server.
This brief tutorial describes how to share the same port for https, ssh using SSLH in Unix-like operating systems.
SSLH – Share The Same Port For HTTPS, SSH, And OpenVPN Install SSLH
SSLH is packaged for most Linux distributions, so you can install it using the default package managers.
On Arch Linux and derivatives like Antergos, Manjaro Linux, install it using Pacman as shown below.
sudo pacman -S sslh
On Debian, Ubuntu, and derivatives, run:
sudo apt-get install sslh
On RHEL, CentOS, you need to add EPEL repository and then install SSLH as shown below.
sudo yum install epel-release
sudo yum install sslh
On Fedora:
sudo dnf install sslh
The output should look like this:
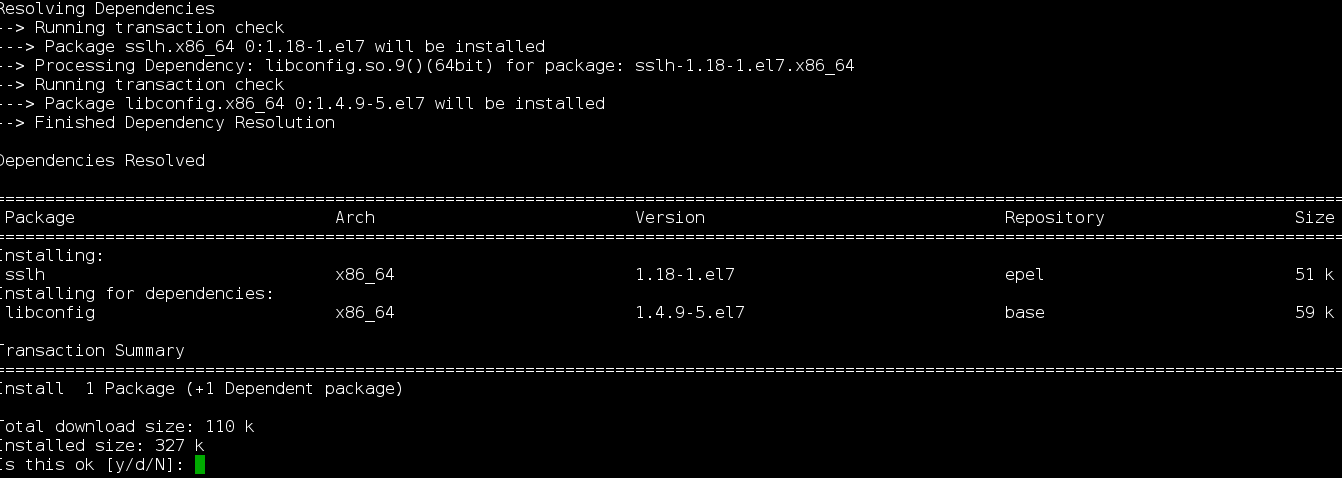
Configure Apache or Nginx webservers
As you already know, Apache and Nginx webservers will listen on all network interfaces (i.e 0.0.0.0:443) by default. We need to change this setting to tell the webserver to listen on the localhost interface only (i.e 127.0.0.1:443 or localhost:443).
To do so, edit the webserver (nginx or apache) configuration file and find the following line:
listen 443 ssl;
And, change it to:
listen 127.0.0.1:443 ssl;
If you’re using Virutalhosts in Apache, make sure you have changed that it too.
VirtualHost 127.0.0.1:443
Save and close the config files. Do not restart the services. We haven’t finished yet.
- Configure SSLH
Once you have made the webservers to listen on the local interface only, edit SSLH config file:
nano /etc/sslh.cfg
You may configure various settings here, but the most important adjustment is to put the section with your external address name to "0.0.0.0" which means that service is going to listen to all network addresses on the same server. Other than that you can configure user running and other things. Here is how my config file on test CentOS 7 server looks like:
~]# cat /etc/sslh.cfg
# This is a basic configuration file that should provide
# sensible values for "standard" setup.
verbose: false;
foreground: true;
inetd: false;
numeric: false;
transparent: false;
timeout: 2;
user: "root";
# Change hostname with your external address name.
listen:
(
{ host: "0.0.0.0"; port: "443"; }
);
protocols:
(
{ name: "ssh"; service: "ssh"; host: "malizeleni1.mylabserver.com"; port: "22"; },
{ name: "openvpn"; host: "malizeleni1.mylabserver.com"; port: "1194"; },
{ name: "xmpp"; host: "malizeleni1.mylabserver.com"; port: "5222"; },
{ name: "http"; host: "malizeleni1.mylabserver.com"; port: "80"; },
{ name: "ssl"; host: "malizeleni1.mylabserver.com"; port: "443"; log_level: 0; },
{ name: "anyprot"; host: "malizeleni1.mylabserver.com"; port: "443"; }
);
Save and close the file.
Now enable sslh service and start it:
systemctl enable sslh
And start it:
systemctl start sslh
You may use lsof command to see what is now listening on the 443 port:
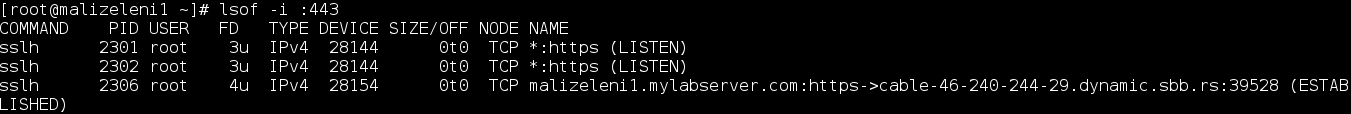
And now you can test and connect to your server and use Multiplexer service:
> ssh -p 443 user@malizeleni1.mylabserver.com
user@malizeleni1.mylabserver.com's password:
Last login: Sun Nov 12 20:44:07 2017 from cable-xx-2x0-2x4-2x.dynamic.sbb.rs
[user@malizeleni1 ~]$ hostname
malizeleni1.mylabserver.com
[user@malizeleni1 ~]$
You are now able to access the remote server via SSH even if the default SSH port 22 is blocked. As you see in the above example, I have used the https port 443 for SSH connection. Also, we can use the same port 443 for OpenVPN connections too. For more details, check the project’s website URL given below.
Alternatively, you can adjust/swap your Nginx and/or Apache to alternative port (for ex 4433 or whatever) and then adjust the sslh.cfg file with that port, for example:
{ name: "ssl"; host: "localhost"; port: "4433"; log_level: 0; },
You may done the same with any other service/port and/or protocol and use this Multiplexer in that purpose.
Cheers!
Resource:
SSLH website (http://www.rutschle.net/sslh)
Hope this article helps you to organize more secure environment within your corporate and/or private network, or at least to override when using public Wi-Fi hotspots.